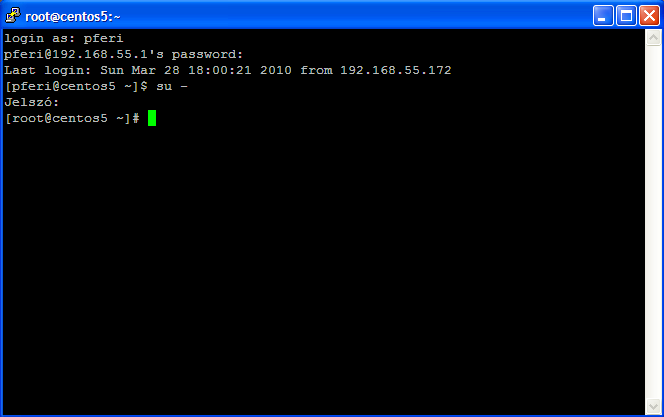
11.1. ábra
| [root@centos5 ~]# chkconfig --list | grep 5:be | sort | cat -n |
| [root@centos5 ~]# chkconfig pcscd off [root@centos5 ~]# chkconfig bluetooth off [root@centos5 ~]# chkconfig hidd off [root@centos5 ~]# chkconfig nfslock off [root@centos5 ~]# chkconfig portmap off [root@centos5 ~]# chkconfig rpcgssd off [root@centos5 ~]# chkconfig rpcidmapd off [root@centos5 ~]# chkconfig sendmail off |
| [root@centos5 ~]# yum install postfix [root@centos5 ~]# yum remove sendmail* [root@centos5 ~]# chkconfig --levels 235 postfix on |
| myhostname = suliserver.suli.uz.ua |
| [root@centos5 ~]# service postfix start |
| #PermitRootLogin yes |
| PermitRootLogin no |
| UseDNS no |
| [root@centos5 ~]# service sshd restart |

| [root@centos5 ~]# mcedit /etc/sysconfig/syslog |
| KLOGD_OPTIONS="-2 -c 1" |
| [root@centos5 ~]# service syslog restart |
| [root@server ~]# head -7 /etc/sysctl.conf # Kernel sysctl configuration file for Red Hat Linux # # For binary values, 0 is disabled, 1 is enabled. See sysctl(8) and # sysctl.conf(5) for more details. # Controls IP packet forwarding net.ipv4.ip_forward = 0 |
| [root@centos5 ~]# service network restart A(z) eth0 csatoló leállítása: [ OK ] A(z) eth1 csatoló leállítása: [ OK ] A visszacsatolási eszköz leállítása: [ OK ] Visszacsatolási eszköz indítása: [ OK ] A(z) eth0 csatoló aktiválása: [ OK ] A(z) eth1 csatoló aktiválása: [ OK ] [root@centos5 ~]# |
| [root@centos5 ~]# chown root:root /root/tuzfal.scp [root@centos5 ~]# chmod 755 /root/tuzfal.scp |
| [root@centos5 ~]# host smtp.bereg.net.ua smtp.bereg.net.ua has address 194.88.152.1 [root@centos5 ~]# host pop3.bereg.net.ua pop3.bereg.net.ua has address 194.88.152.2 |
| [root@centos5 ~]# /root/tuzfal.scp start indul.... ---------------------------------------------------------------- A belso halo: 192.168.55.0/24 ---------------------------------------------------------------- A tuzfal BELSO halokartyaja: eth1 inet addr:192.168.55.1 Bcast:192.168.55.255 Mask:255.255.255.0 ---------------------------------------------------------------- A tuzfal KULSO halokartyaja: eth0 inet addr:192.168.4.2 Bcast:192.168.4.3 Mask:255.255.255.252 ---------------------------------------------------------------- A tuzfal csomagszuroinek betoltese [root@centos5 ~]# |
| $IPTABLES -A INPUT -p tcp -i $IFACE_INT -s $NET_INT --dport 80 -m state --state NEW -j ACCEPT |
| [root@centos5 ~]# service iptables save A tűzfalszabályok mentése ide: /etc/sysconfig/iptables: [ OK ] |
| [root@centos5 ~]# service iptables status |
| [root@centos5 ~]# echo "/root/tuzfal.scp start" >> /etc/rc.d/rc.local |
| $IPTABLES -A FORWARD -s $GEPIP2 -j ACCEPT |
| # CIMFORDITAS gmail levelek ki + log $IPTABLES -t nat -A POSTROUTING -s $GEPIP2 -p tcp --dport 465 -o $IFACE_EXT -j LOG --log-prefix "gmail ki-g2 " $IPTABLES -t nat -A POSTROUTING -s $GEPIP2 -p tcp --dport 465 -o $IFACE_EXT -j SNAT --to-source $IP_EXT # CIMFORDITAS gmail levelek be + log $IPTABLES -t nat -A POSTROUTING -s $GEPIP2 -p tcp --dport 995 -o $IFACE_EXT -j LOG --log-prefix "gmail be-g2 " $IPTABLES -t nat -A POSTROUTING -s $GEPIP2 -p tcp --dport 995 -o $IFACE_EXT -j SNAT --to-source $IP_EXT |
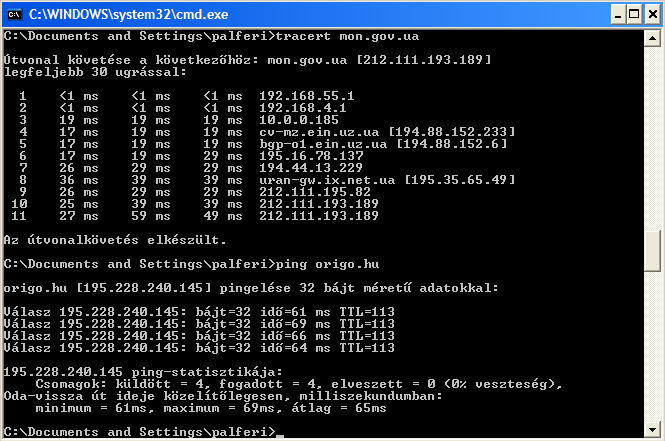
| [root@centos5 ~]# tail -f /var/log/messages Mar 29 00:13:41 centos5 kernel: NAT icmp g2 IN= OUT=eth0 SRC=192.168.55.172 DST=212.111.193.189 LEN=92 TOS=0x00 PREC=0x00 TTL=1 ID=9254 PROTO=ICMP TYPE=8 CODE=0 ID=768 SEQ=65281 Mar 29 00:14:44 centos5 kernel: NAT icmp g2 IN= OUT=eth0 SRC=192.168.55.172 DST=195.228.240.145 LEN=60 TOS=0x00 PREC=0x00 TTL=127 ID=9328 PROTO=ICMP TYPE=8 CODE=0 ID=768 SEQ=15874 Mar 29 00:14:45 centos5 kernel: NAT icmp g2 IN= OUT=eth0 SRC=192.168.55.172 DST=195.228.240.145 LEN=60 TOS=0x00 PREC=0x00 TTL=127 ID=9329 PROTO=ICMP TYPE=8 CODE=0 ID=768 SEQ=16130 Mar 29 00:14:46 centos5 kernel: NAT icmp g2 IN= OUT=eth0 SRC=192.168.55.172 DST=195.228.240.145 LEN=60 TOS=0x00 PREC=0x00 TTL=127 ID=9330 PROTO=ICMP TYPE=8 CODE=0 ID=768 SEQ=16386 Mar 29 00:14:48 centos5 kernel: NAT icmp g2 IN= OUT=eth0 SRC=192.168.55.172 DST=195.228.240.145 LEN=60 TOS=0x00 PREC=0x00 TTL=127 ID=9331 PROTO=ICMP TYPE=8 CODE=0 ID=768 SEQ=16642 |
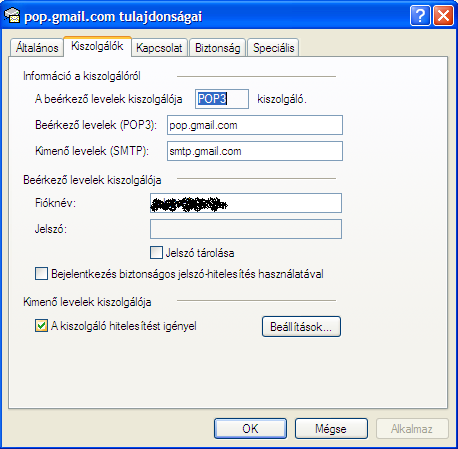
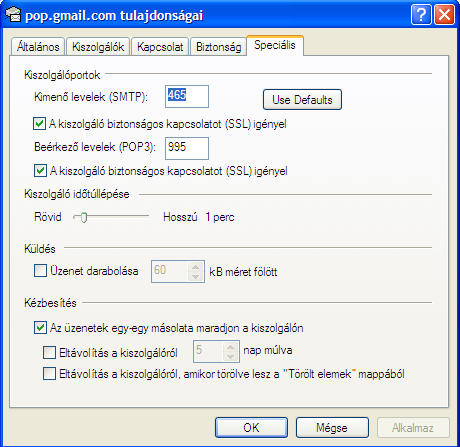
| [root@centos5 ~]# tail -f /var/log/messages Mar 29 00:40:32 centos5 kernel: gmail ki-g2 IN= OUT=eth0 SRC=192.168.55.172 DST=209.85.129.109 LEN=48 TOS=0x00 PREC=0x00 TTL=127 ID=9449 DF PROTO=TCP SPT=1159 DPT=465 WINDOW=65535 RES=0x00 SYN URGP=0 Mar 29 00:40:40 centos5 kernel: gmail ki-g2 IN= OUT=eth0 SRC=192.168.55.172 DST=209.85.129.109 LEN=48 TOS=0x00 PREC=0x00 TTL=127 ID=9490 DF PROTO=TCP SPT=1161 DPT=465 WINDOW=65535 RES=0x00 SYN URGP=0 Mar 29 00:40:47 centos5 kernel: gmail be-g2 IN= OUT=eth0 SRC=192.168.55.172 DST=72.14.221.111 LEN=48 TOS=0x00 PREC=0x00 TTL=127 ID=9563 DF PROTO=TCP SPT=1163 DPT=995 WINDOW=65535 RES=0x00 SYN URGP=0 |
| $IPTABLES -A FORWARD -s $GEPIP1 -j ACCEPT $IPTABLES -t nat -A POSTROUTING -s $GEPIP1 -o $IFACE_EXT -j LOG --log-prefix "NAT-gep1 " $IPTABLES -t nat -A POSTROUTING -s $GEPIP1 -o $IFACE_EXT -j SNAT --to-source $IP_EXT |
| [root@server ~]# /root/tuzfal.scp start |
| [root@server ~]# service iptables save |
| #!/bin/bash # Vezessunk be nehany valtozot: IFACE_EXT=eth0 IFACE_INT=eth1 NET_INT=192.168.55.0/24 # kulso, belo IP cim, SMTP, POP3 serverek: IP_EXT=192.168.4.2 IP_INT=192.168.55.1 SMTPIP=194.88.152.1 POP3IP=194.88.152.2 # Nehany spec. gep a belso halon: GEPIP1=192.168.55.101 GEPIP2=192.168.55.172 GEPIP3=192.168.55.182 # IPTABLES=/sbin/iptables case "$1" in start) echo "indul...." # Nehany biztonsagi beallitas: # Enable broadcast echo protection echo 1 > /proc/sys/net/ipv4/icmp_echo_ignore_broadcasts # Disable source routed packets for f in /proc/sys/net/ipv4/conf/*/accept_source_route; do echo 0 > $f done # Enable TCP SYN cookie protection echo 1 > /proc/sys/net/ipv4/tcp_syncookies # Disable ICMP Redirect acceptance for f in /proc/sys/net/ipv4/conf/*/accept_redirects; do echo 0 > $f done # Don't send Redirect messages for f in /proc/sys/net/ipv4/conf/*/send_redirects; do echo 0 > $f done # Drop spoofed packets coming in on an interface, which if replied to, # would result in the reply going out a different interface for f in /proc/sys/net/ipv4/conf/*/rp_filter; do echo 1 > $f done # Log packets with impossible addresses for f in /proc/sys/net/ipv4/conf/*/log_martians; do echo 1 > $f done # IP-tovabbitas a kernelben echo 1 > /proc/sys/net/ipv4/ip_forward echo "----------------------------------------------------------------" echo "A belso halo:" $NET_INT echo "----------------------------------------------------------------" echo " A tuzfal BELSO halokartyaja: " $IFACE_INT /sbin/ifconfig $IFACE_INT | grep "inet addr" echo "----------------------------------------------------------------" echo " A tuzfal KULSO halokartyaja: " $IFACE_EXT /sbin/ifconfig $IFACE_EXT | grep "inet addr" echo "----------------------------------------------------------------" echo "A tuzfal csomagszuroinek betoltese" # Eloszor a kernel modulokat toltjuk be: /sbin/modprobe ip_tables /sbin/modprobe ip_conntrack_ftp /sbin/modprobe iptable_nat /sbin/modprobe ip_nat_ftp # A regi szabalyokat es a regi egyeni tablakat toroljuk $IPTABLES --flush $IPTABLES --delete-chain $IPTABLES --flush -t nat $IPTABLES --delete-chain -t nat $IPTABLES -t mangle -F $IPTABLES -X # # Alapertelmezett visszautasitasi szabalyok $IPTABLES -P INPUT DROP $IPTABLES -P FORWARD DROP $IPTABLES -P OUTPUT DROP # # A loopback interface-nek szabad kezet $IPTABLES -I INPUT -i lo -j ACCEPT $IPTABLES -I OUTPUT -o lo -j ACCEPT # #----------------------------------------------------------------------- # Beerkezo szabalyok #----------------------------------------------------------------------- # A korabban mar jovahagyott kapcsolatok reszekent beerkezo csomagok elfogadasa $IPTABLES -A INPUT -j ACCEPT -m state --state ESTABLISHED,RELATED # # Minden TCP kapcsolatnak a SYN kifejezessel kell kezdodnie: $IPTABLES -A INPUT -p tcp ! --syn -m state --state NEW -j LOG --log-prefix "Rejt. letepogatasi kiserlet?" $IPTABLES -A INPUT -p tcp ! --syn -m state --state NEW -j DROP # Webservert a belso halora $IPTABLES -A INPUT -p tcp -i $IFACE_INT -s $NET_INT --dport 80 -m state --state NEW -j ACCEPT # POP3 $IPTABLES -A INPUT -p tcp -i $IFACE_INT -s 192.168.55.172 --dport 110 -m state --state NEW -j ACCEPT # SSH a belso halorol. Ezt lehetne korlatozni IP(k)-re... $IPTABLES -A INPUT -p tcp -i $IFACE_INT -s $NET_INT --dport 22 -m state --state NEW -j ACCEPT # # SMTP a belso halorol + log. Ezt lehetne korlatozni IP(k)-re... $IPTABLES -A INPUT -p tcp -i $IFACE_INT -s $NET_INT --dport 25 -m state --state NEW -j LOG --log-prefix " level SMTP" $IPTABLES -A INPUT -p tcp -i $IFACE_INT -s $NET_INT --dport 25 -m state --state NEW -j ACCEPT # A DNS-t a belso gepeknek $IPTABLES -A INPUT -p udp -s $NET_INT --dport 53 -m state --state NEW -j ACCEPT $IPTABLES -A INPUT -p tcp -s $NET_INT --dport 53 -m state --state NEW -j ACCEPT # SAMBA a belso gepeknek $IPTABLES -A INPUT -p udp -s $NET_INT --dport 137 -m state --state NEW -j ACCEPT $IPTABLES -A INPUT -p udp -s $NET_INT --dport 138 -m state --state NEW -j ACCEPT $IPTABLES -A INPUT -p tcp -s $NET_INT --dport 139 -m state --state NEW -j ACCEPT $IPTABLES -A INPUT -p tcp -s $NET_INT --dport 445 -m state --state NEW -j ACCEPT # DHCP server $IPTABLES -A INPUT -p udp -s $NET_INT --dport 67 -m state --state NEW -j ACCEPT # Pingek a belso halozatnak $IPTABLES -A INPUT -s $NET_INT -p icmp -j ACCEPT # Pingek kivulrol $IPTABLES -A INPUT -i $IFACE_EXT -p icmp -j ACCEPT # Proxy hozzaferes a belso halonak: $IPTABLES -A INPUT -p tcp -i $IFACE_INT -s $NET_INT --dport 8080 -m state --state NEW -j ACCEPT # Naplozz mindent, amit fent elutasitottal: $IPTABLES -A INPUT -j LOG --log-prefix "Visszautasitva (INPUT):" $IPTABLES -A INPUT -j DROP # #---------------------------------------------------------------------- # Kimeno szabalyok #---------------------------------------------------------------------- # Amennyiben jovahagyott kapcsolatok reszet kepezik, engedd ki $IPTABLES -A OUTPUT -m state --state RELATED,ESTABLISHED -j ACCEPT # A kimeno pingek engedelyezese $IPTABLES -A OUTPUT -p icmp -j ACCEPT # Kimeno traceroute $IPTABLES -A OUTPUT -p udp --sport 1024:65535 -d 0/0 --dport 33434:33523 -j ACCEPT # A kimeno DNS lekerdezesek engedelyezese: $IPTABLES -A OUTPUT -p udp --dport 53 -j ACCEPT # A kimeno http engedelyezese: $IPTABLES -A OUTPUT -p tcp --dport 80 -j ACCEPT # A kimeno https engedelyezese $IPTABLES -A OUTPUT -p tcp --dport 443 -j ACCEPT # A kimeno ssh engedelyezese # $IPTABLES -A OUTPUT -p tcp --destination-port 22 -j ACCEPT # A kimeno ftp engedelyezese $IPTABLES -A OUTPUT -p tcp --dport 21 -j ACCEPT # A kimeno mail engedelyezese + log $IPTABLES -A OUTPUT -p tcp --dport 25 -j LOG --log-prefix "mail-ki " $IPTABLES -A OUTPUT -p tcp --dport 25 -j ACCEPT # # SAMBA $IPTABLES -A OUTPUT -p udp -d $NET_INT --dport 137 -j ACCEPT $IPTABLES -A OUTPUT -p udp -d $NET_INT --dport 138 -j ACCEPT $IPTABLES -A OUTPUT -p tcp -d $NET_INT --dport 139 -j ACCEPT $IPTABLES -A OUTPUT -p tcp -d $NET_INT --dport 445 -j ACCEPT $IPTABLES -A OUTPUT -p udp -d $NET_INT --sport 137 -j ACCEPT $IPTABLES -A OUTPUT -p tcp -d $NET_INT --sport 139 -j ACCEPT $IPTABLES -A OUTPUT -p tcp -d $NET_INT --sport 445 -j ACCEPT # # NTP (pontos ido keres + log) $IPTABLES -A OUTPUT -p udp --dport 123 -j LOG --log-prefix "ntp-kiszolgalohoz " $IPTABLES -A OUTPUT -p udp --dport 123 -j ACCEPT # # Naplozz mindent, amit elutasitottal: $IPTABLES -A OUTPUT -j LOG --log-prefix "Visszautasitva (OUTPUT):" $IPTABLES -A OUTPUT -j DROP # #---------------------------------------------------------------------- # Tovabbitasi szabalyok #---------------------------------------------------------------------- # A korabban mar jovahagyott kapcsolatok reszekent tovabbitando csomagok $IPTABLES -A FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT # # Minden TCP kapcsolatnak a SYN kifejezessel kell kezdodnie: $IPTABLES -A FORWARD -p tcp ! --syn -m state --state NEW -j LOG --log-prefix "Letepogatasi kiserlet?" $IPTABLES -A FORWARD -p tcp ! --syn -m state --state NEW -j DROP # # ------------------------------------------ A GEP2 beallitasai ------------------------ $IPTABLES -A FORWARD -s $GEPIP2 -j ACCEPT # CIMFORDITAS Levelek ki + log $IPTABLES -t nat -A POSTROUTING -s $GEPIP2 -d $SMTPIP -p tcp --dport 25 -o $IFACE_EXT -j LOG --log-prefix "mail ki-g2 " $IPTABLES -t nat -A POSTROUTING -s $GEPIP2 -d $SMTPIP -p tcp --dport 25 -o $IFACE_EXT -j SNAT --to-source $IP_EXT # CIMFORDITAS Levelek be + log $IPTABLES -t nat -A POSTROUTING -s $GEPIP2 -d $POP3IP -p tcp --dport 110 -o $IFACE_EXT -j LOG --log-prefix "mail be-g2 " $IPTABLES -t nat -A POSTROUTING -s $GEPIP2 -d $POP3IP -p tcp --dport 110 -o $IFACE_EXT -j SNAT --to-source $IP_EXT # CIMFORDITAS gmail levelek ki + log $IPTABLES -t nat -A POSTROUTING -s $GEPIP2 -p tcp --dport 465 -o $IFACE_EXT -j LOG --log-prefix "gmail ki-g2 " $IPTABLES -t nat -A POSTROUTING -s $GEPIP2 -p tcp --dport 465 -o $IFACE_EXT -j SNAT --to-source $IP_EXT # CIMFORDITAS gmail levelek be + log $IPTABLES -t nat -A POSTROUTING -s $GEPIP2 -p tcp --dport 995 -o $IFACE_EXT -j LOG --log-prefix "gmail be-g2 " $IPTABLES -t nat -A POSTROUTING -s $GEPIP2 -p tcp --dport 995 -o $IFACE_EXT -j SNAT --to-source $IP_EXT # Ping, traceroute (csak ha kell) $IPTABLES -t nat -A POSTROUTING -s $GEPIP2 -p icmp -o $IFACE_EXT -j LOG --log-prefix "NAT icmp g2 " $IPTABLES -t nat -A POSTROUTING -s $GEPIP2 -p icmp -o $IFACE_EXT -j SNAT --to-source $IP_EXT # --------------------------------------------------------------------------------------- # # Syn-flood elleni vedelem: $IPTABLES -A FORWARD -p tcp --syn -m limit --limit 1/s -j ACCEPT # Portscan elleni vedelem: $IPTABLES -A FORWARD -p tcp --tcp-flags SYN,ACK,FIN,RST RST -m limit --limit 1/s -j ACCEPT # Ping-flood elleni vedelem: $IPTABLES -A FORWARD -p icmp --icmp-type echo-request -m limit --limit 1/s -j ACCEPT # Logoljuk amit nem FORWARD-ol $IPTABLES -A FORWARD -j LOG --log-prefix "Visszautasit(FWD)! " $IPTABLES -A FORWARD -j DROP # ;; # Ez az amit nem szabad: open) echo "VIGYAZAT! A tuzfal kikapcsolasa! MEGORULTEL??!!" # $IPTABLES --flush $IPTABLES --delete-chain $IPTABLES --flush -t nat $IPTABLES --delete-chain -t nat $IPTABLES -t mangle -F $IPTABLES -X # $IPTABLES -P INPUT ACCEPT $IPTABLES -P FORWARD ACCEPT $IPTABLES -P OUTPUT ACCEPT ;; # Kikapcsol minden tuzfalszabalyt, csak az alapertelmezett elutasitas marad # Kenelben IP-tovabbitas ki stop) echo "A tuzfal leallitasa zart allapotban!" echo 0 > /proc/sys/net/ipv4/ip_forward $IPTABLES --flush ;; status) echo "A iptables allapotanak lekerdezese..." echo " (valojaban az iptables-save parancs vegrehajtasa)..." $IPTABLES-save ;; restart|reload) $0 stop $0 start ;; *) echo "Statusz: $0 {start|open|stop|status|restart|reload}" exit 1 ;; esac exit 0 |